Task #2105
closed
Dynamic form for identities
100%
Description
Feature will cover requirement to configure different form to create and edit different type of identity (externist vs. internist):
- new field with type (~codelist) will be added to identity - will control, which form will be used
- identity type can be switched - new identity permission will be added
- new type can be registered (~by codelist item)
- when new identity is created, then modal window with available identity types will be shown. If only one type is available => then form will be shown imediatelly (=> default / current form will be shown).
Files
Related issues
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
- Related to Task #2153: Autorization policies - add evaluator by user type (projection) added
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
- Related to Task #2154: Automatic roles: Support user type field (projection) in automatic role by attribute added
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
- Related to Task #2155: Support user type field (projection) in synchronization and provisioning added
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
- % Done changed from 0 to 80
Form projection feature is implemented and merged into develop:
https://github.com/bcvsolutions/CzechIdMng/commit/9bcd313a681295a2122ed7d4668cd71685bae6a5
Documentation remains, will be here:
https://wiki.czechidm.com/devel/documentation/identities/adm/user-type
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
- Status changed from In Progress to Needs feedback
- Assignee changed from Radek Tomiška to Vít Švanda
- % Done changed from 80 to 90
Commit:
https://github.com/bcvsolutions/CzechIdMng/commit/9bcd313a681295a2122ed7d4668cd71685bae6a5
Documentation entry point is here:
https://wiki.czechidm.com/devel/documentation/identities/adm/user-type
Could you provide me a feedback, please?
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
- Related to Task #2162: Bulk action - change user type (projection) added
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
- Related to Task #2163: Authorization policies - support secured contract eav attributes by default added
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
- Related to Task #2164: Authorization policies - support secured identity eav attributes by default added
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
- Related to Task #2165: Authorization policies - check change user type permission on backend added
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
Fixed review notes:
- authorities was evaluated only on form projection => permissions were ignored
- user type is removed from basic fields available for form projection
- username is required for updata by projection (the same behavior as defaul form)
- doc improved, update identity permission is needed to submit projection form (can be improved in future)
Commit:
https://github.com/bcvsolutions/CzechIdMng/commit/e8b7d45802711ceb48a093a9b8bbf840eaa6f632
 Updated by Vít Švanda over 4 years ago
Updated by Vít Švanda over 4 years ago
- File projection_one_full.png projection_one_full.png added
- File projection_one.png projection_one.png added
- Status changed from Needs feedback to In Progress
- Assignee changed from Vít Švanda to Radek Tomiška
I did review and test. This is very big and complex feature. Works nice and code looks also nice. Nice tutorial! Thanks for this.
I tested again the issues we consulted and what you fixed. Everything works well now, expect one thing:
If my user can updated his identity full detail (firstname...), then projection detail can be saved, but identity fields are read-only.
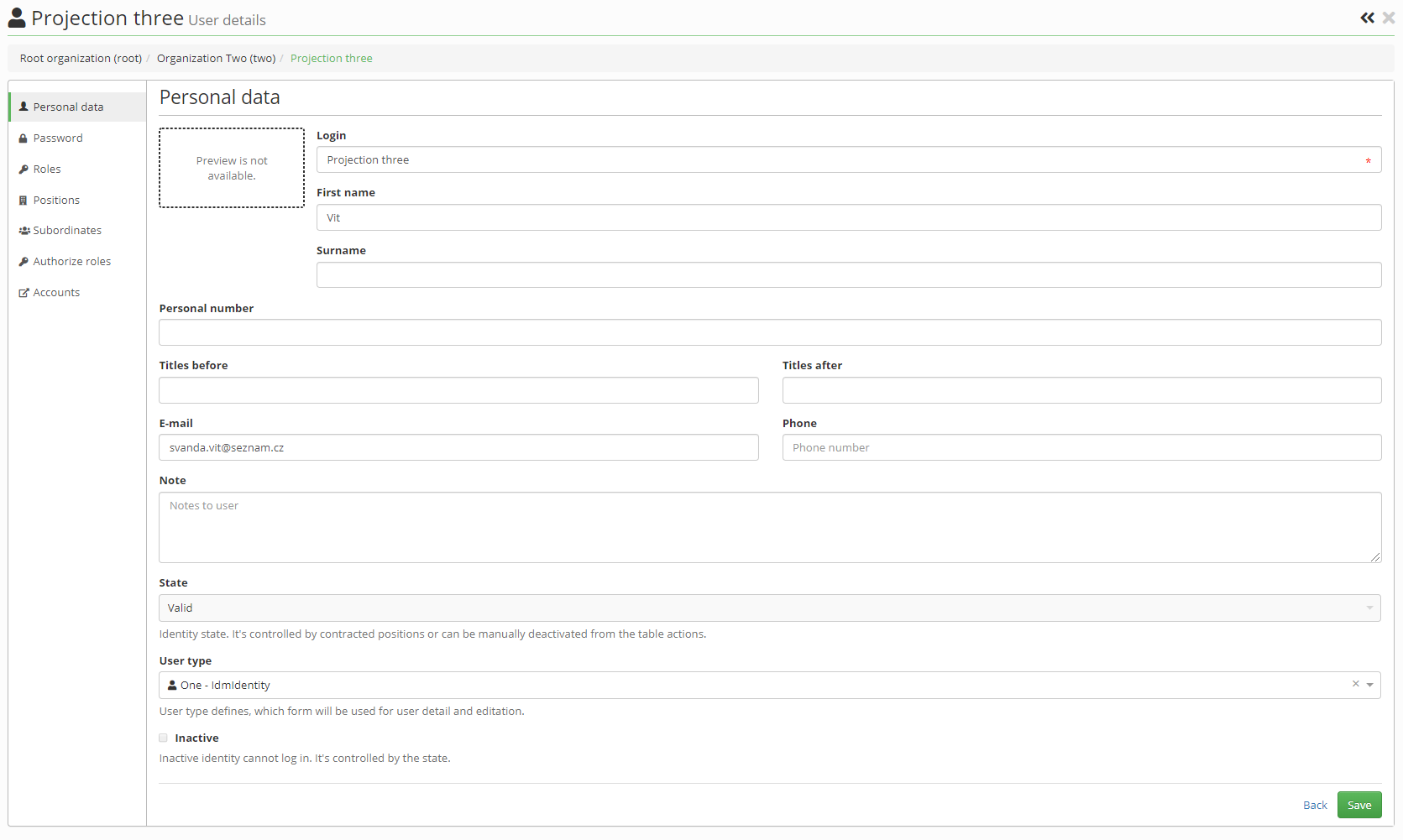

Notes:
- Role with attributes are not fully supported for create new identity now. Maybe warning in the wiki should be created for it.
- You changed version of the selectbox from 1.3 to 1.2. I was a intent?
- Wiki: Should be not IdmFormDefiniton: Permission to autocomplete form projections: Forms - projections(IdmFormDefiniton) | View in select box (autocomplete) | BasePermissionEvaluator
 Updated by Vít Švanda over 4 years ago
Updated by Vít Švanda over 4 years ago
- Related to Defect #2190: Read only on form doesn't work properly - AbstractFrom added
 Updated by Vít Švanda over 4 years ago
Updated by Vít Švanda over 4 years ago
My issues with wrong read only form, is related to AbstractForm and will be solved within #2190. I have removed the readOnly property "workaround". The form now works correctly.
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
- Status changed from In Progress to Resolved
- % Done changed from 90 to 100
Thx for help! I retest permissions again and workaround works.
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
- Status changed from Resolved to Closed
 Updated by Radek Tomiška over 4 years ago
Updated by Radek Tomiška over 4 years ago
- Related to Feature #891: Identity templates module added
 Updated by Radek Tomiška about 4 years ago
Updated by Radek Tomiška about 4 years ago
- Related to Defect #2567: Automatic role by EAV is not assigned when setting the EAV together with entity (e.g. through form projection) added